contact us
Abacus Quality System Services, Inc.
6161 Savoy Drive, Suite 455,
Houston, TX 77036
USA
Historically, Vulnerability Management used to be a function of server operations and application support groups. Over time, the emergence of new technology gave rise to online data-sharing concepts and cloud computing, and the lines between on-prem and cloud-based assets started to blur. The proliferation of mobile devices accessing company networks with the concept of BYOD, it became increasingly harder for asset/app owners to get their hands around the roles and responsibilities to keep all the devices and apps at the latest patch levels while mitigating the production demands on systems. In the present day, it has become unavoidable and mandatory to treat Vulnerability Management as a separate entity rather than a function of some existing operations group. Most enterprise businesses already have some variant of Vulnerability Management programs in place, with a few reaching maturity due to the relatively liquid nature of the IT infrastructure landscape and the ever-evolving nature of threats and vulnerabilities.
IT security regulations are increasingly the norm and demonstrate a standard of care in protecting sensitive data. To serve this standard, several regulatory bodies have mandated the creation of Vulnerability Management Programs. Examples include the Payment Card Industry Data Security Standard (PCI DSS), Health Insurance Portability and Accountability Act (HIPAA), and Federal Energy Regulation Committee (FERC).
Vulnerability Management Programs address the inherent security weakness created by software vulnerabilities. Known software vulnerabilities create opportunities for criminals and other adversaries to exploit these weaknesses. These vulnerabilities may result in unauthorized access to a system / network or access to confidential data which would result in regulatory, financial, or reputational impacts on the business. Unfortunately, new software vulnerabilities are discovered daily.
Vulnerability Management (VM) is the means of detecting, removing, and controlling the inherent risk of vulnerabilities. A well-designed Vulnerability Management Program utilizes specialized software and workflow to help eliminate detected risks.
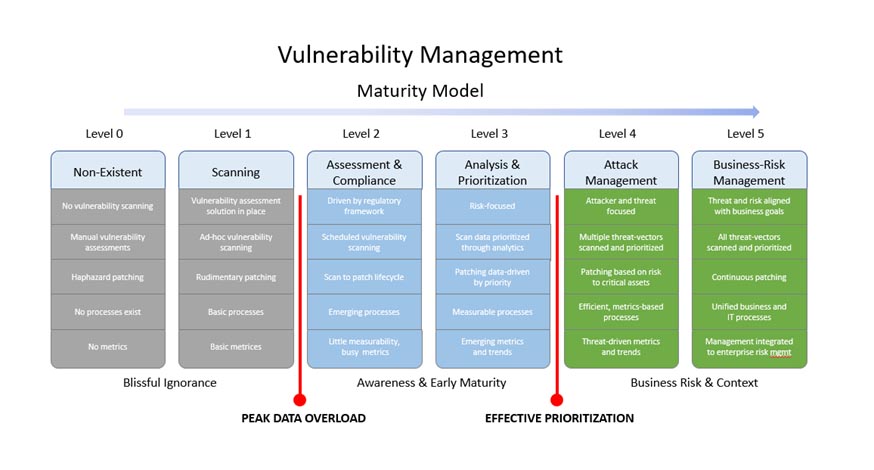
A good Vulnerability Management Program should have the following components:
Regardless of what your vulnerability management program looks like, we can help.
We will be happy to give you more information about our services. Please fill in this form to contact us. We will respond as soon as possible.
Abacus Quality System Services, Inc.
6161 Savoy Drive, Suite 455,
Houston, TX 77036
USA